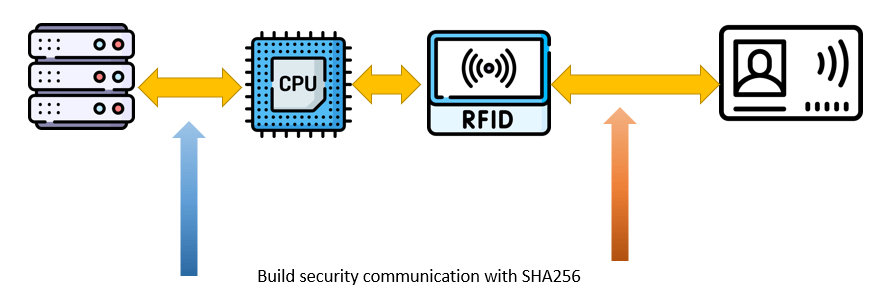
To summarize this project. This project has introduced an RFID access system with security solutions. This project has targeted some common threats and implement the security solution into the RFID access systems. With the development of science and technology, attacker must have more chance to attack on RFID technology. Moreover, with the development of technology. Attacker must have more tools to attack on RFID technology. Although some of the attack like eavesdropping, man-in-the-middle attack, spoofing cannot deter them by the existing technology. But with the solution provide in this project, it must increase the difficulties for attacker to attack.
Moreover, during this project. This secure RFID access systems is suitable for different situation. It supplies a two step authorization system. With the existing technology, two step authorization system is out of the most secure authorization systems. It is because the attacker needs to spend more time on attacking to compare with single authorization systems. The cost performance ratio is not high enough for attacker to spend lots of time to attack. Therefore, this system is suitable for different situation, like home, office, school, etc.
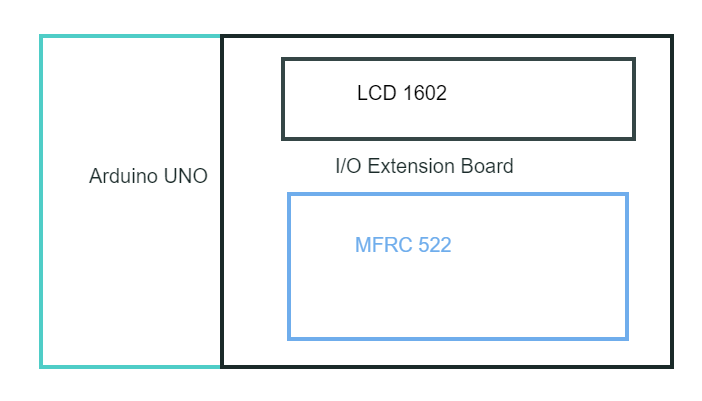
But in the future, this project must have some place can be improved. First, I choose to use Arduino UNO as my main control board is because Arduino is a company that focus on microcontroller. Moreover, it is open sources. Therefore, Arduino must have the best support and community compare with another brand. But during the project, I figure out that Arduino doesn't provide any security solution. Moreover, Arduino IDE is using C and C+ programming language. But with the development of libraries, more and more libraries prefer to using C# and python as the programming language. It is because those programming provide a better performance. Although the Arduino has provided a convert language function, but while converting. It has a high chance that would crash or has error.
Therefore, maybe using Raspberry Pi maybe would has a better performance than Arduino. Raspberry Pi is a small single-board computers. It can support C, C+, C#, Python 2 and Python 3. Moreover, the specification is much better than Arduino. For example, Raspberry Pi can have at most 8 GB memory. But Arduino only support 32MB memory. Therefore, more function and more security solution can be done within Raspberry Pi. Also, since Raspberry Pi support lots of programming languages. It has more libraries support than Arduino.
Second, can replace other physical security solution than using embed systems. Using embed system can provide a strong security solution. During the project, I figure out that actually is hard to install the embed systems. By using embed systems. It needs to cut a place from the door to place the system. Therefore, the cost of using these systems become higher. Moreover, if need to upgrade the systems or adding more modules. It needs to reinstall the systems again. The cost performance ratio of embed system are not good enough. Maybe using another solution can provide a better cost performance ratio than embed system.