The project includes several key goals that should be met, and this session would outline all the goals that must be met throughout the course of the project, as well as briefly discuss the steps that would be done to reach each goal and what each goal entails.
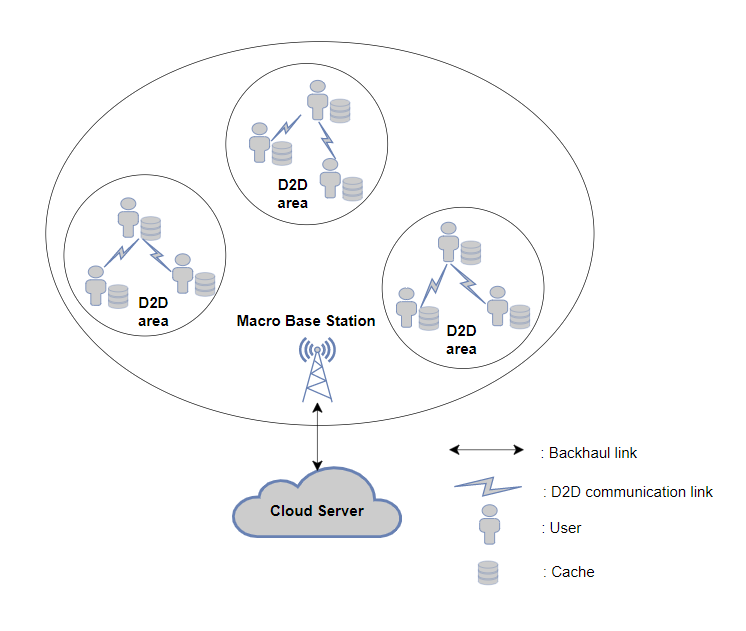
The theme of this project is the performance optimization of cache aware D2D communication system, in order to achieve the performance optimization, we need to solve the problem of maximizing the cache hit ratio.
First, the background of this problem should be analyzed, such as the operation principle of the D2D system. Understand the problem background and related concepts in order to propose a solution to the project topic.
In addition, past literature must be studied to understand what factors have been considered in the past on related issues, to find out what can be improved and what can be referred to in this project. Define the difference between this project and the previous studies. Previous literature describes on D2D systems and caching systems to identify various indicators that can affect the performance of the system and ways to improve it. Finally, explain why the optimization problem will be NP-hard level by related literature.
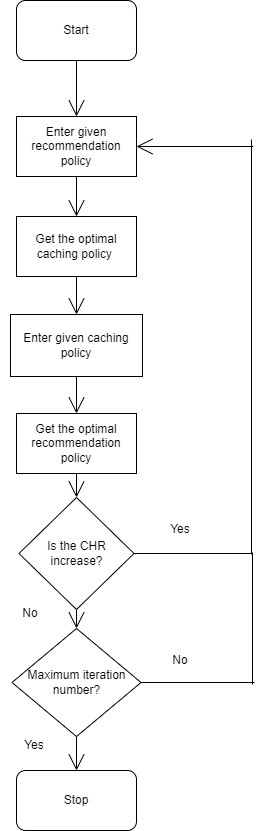
In the solution design we define the system model, identify and explain the elements that need to be considered to maximize the cache hit rate, explain the significance of recommendation and cache placement for this project, and finally combine the two problems and maximize the cache hit rate in a swap then compare fashion.
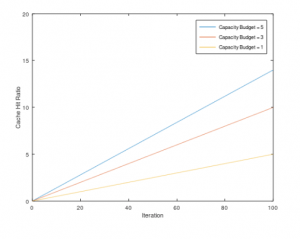
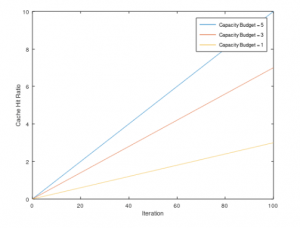
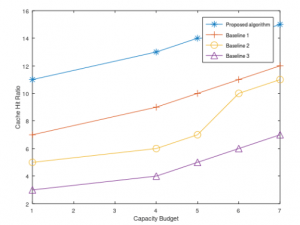
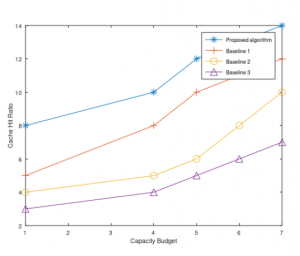
In the section of experiments and results, the steps to simulate the above algorithm using Monte Carlo method would be show and explain, then compare and analyze the results according to different baselines.
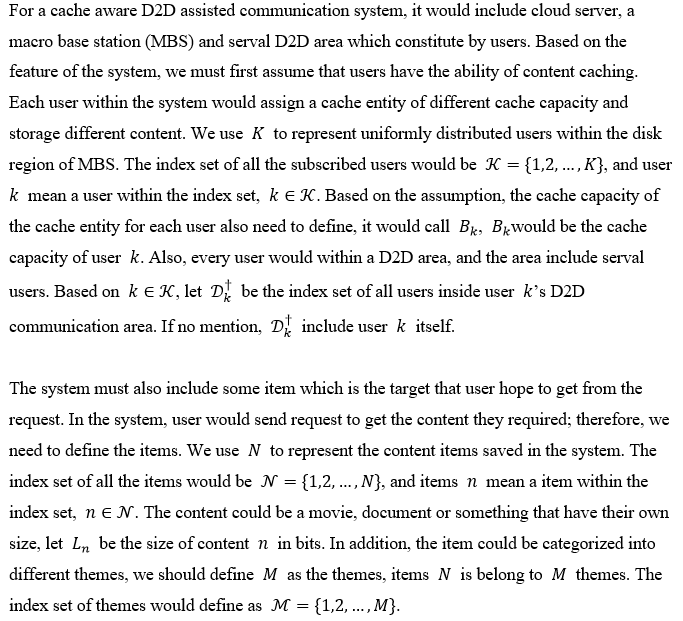
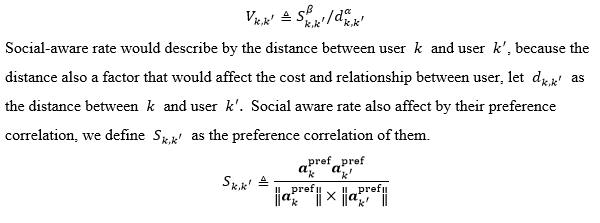
The most important goal that must be achieved is the theme of this project, to optimize the performance of the Cache-aware D2D assisted communication system. To perform performance optimization, it is necessary to understand some important definitions such as cache hit ratio. The first goal to be achieved is to study and explore the background of this project. Only with a deep understanding of the principles of the project, we can analyze the existing situation, discover the existing areas for improvement, and make improvements to the defective areas to achieve performance optimization. Other objectives to be achieved include modeling the social relationships between each user, calculating the set of possible users for a typical user, and problem formulation based on factors such as the distribution of user preferences. Problem formulation is one of the most important objectives to be achieved.
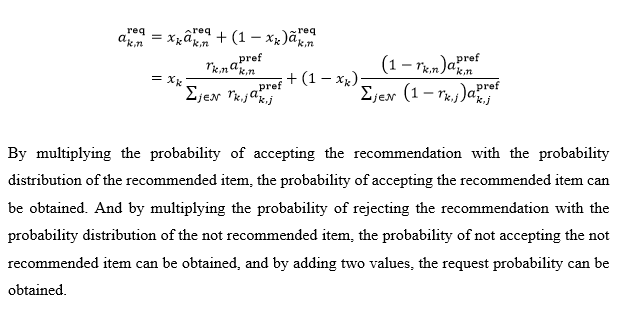
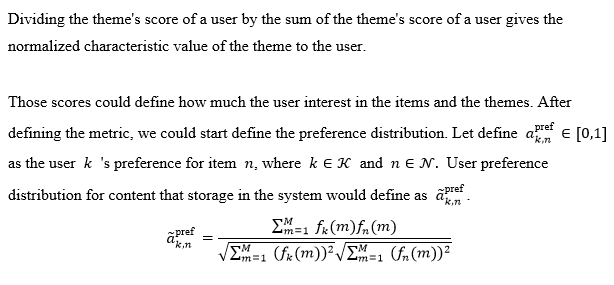
This objective is to present mathematically the various factors in the research topic, including user preferences, user relationships, and factors that affect the user’s decision to transfer data, and to define each of these factors in mathematical form, and finally to perform the formulation. Another goal that needs to be achieved is to propose a solution based on the formulation, i.e., a way to optimize the performance of the main idea of the solution. The objective of the final, simulation is to offer evidence to establish that the findings of this study are viable, as well as data.